Access Control Device
Showing all 2 resultsSorted by latest
Access Control Devices: The Essential Technology for Modern Security and Smart Workplaces
Today, with safety threats and risks to the operation increasing every day, access control devices technology is becoming most essential to the protection of businesses, homes, and organizations. These devices do more than unlock doors, they form an intelligent security perime that aid in the supervision, control, and restriction of access to certain areas at certain times. Whether an office, warehouse, apartment complex, corporate/industrial establishment, access control devices technology makes sure that only legally accepted people gain access and hence eliminates security risks and ensures smooth day-to-day activities. As more and more workplaces become advanced and digital, the need for robust access control technology is increasing exponentially.

Why Access Control Devices Are Critical in Today’s World
The security risks of today are much more complex. The risks of physical intrusion, internal pilfering, unauthorized guests, tailgating, and data breaches are more prominent in organizations that lack effective access control. Access control devices technology are no longer optional. They are a baseline security for any business.
3 Advanced Access Control Concepts
Access Control Entry
Access Control Entry is a complete system for the control and validation of people at a door, gate or perimeter a particular area.
This involves the actual hardware of the card reader and the software decision engine that decides whether to grant the access or not.
Common authentication methods are keycards, key fobs, biometric scans, facial recognition or mobile credentials.
Access Control systems such as Entry generally keep full granular event logs which provides more transparency and security.
Be it offices, homes or factories, they allow you to design and build your own solutions for controlled and predictable flow of users and goods.
Attribute-Based Access Control (ABAC)
ABAC definitionAttribute-Based Access Control (ABAC) is a modern and complex access control model in today’s-evolving security landscape.
Instead of just conventional roles, ABAC takes into account multiple factors such as time and location, user identity, device type, and organization policies.
As an illustration, a worker can get into a server room only during work hours and only on an authorized machine.
This dynamic approach allows access decisions to be context-aware and very accurate,” said O’Connor.“An ABAC-based identity governance platform performs extremely well and scales well.”
ABAC is perfect for entities with complex workflows, sensitive information or security protocols that change frequently.
Access Control Door Lock
The Access Control Door Lock on the physical door turns the hardware to enforce the security policy.
These locks can be magnetic locks, electric strikes, smart deadbolts or even fully wireless IoT-enabled smart locks.
They swap the traditional keys with smart authentication solutions such as fingerprint, mobile app or rfid cards.
Access Control Door Locks add an extra layer of security, as they make it more difficult for an unauthorized person to enter or exit a door with out the lock being disengaged first.
They also are vital for keeping out forced entry, key copying and unauthorized access.
The Importance of Access Control Devices for Modern Office Spaces “Why Modern Offices Can’t Operate Without Access Control Devices?”
The offices in today’s day and age of corporate America have employees, guests, delivery people, and contractors constantly coming and going. Without a good system of access control, controlling who comes into the building or keeping the building secure is a lost cause.
Here’s several reasons why an office or workplace would benefit from having access control:
• To block unauthorized access to staff only areas
• To secure sensitive areas such as server rooms, file storage and finance
• To enable monitoring of staff movement for safety and reporting
• To remove or minimize manual calculations of attendance and thus reduce errors in payroll
• To prevent security breaches due to tailgating or lost keys
• To offer temporary or guest access to the premises
• To ensure a safer workplace for employees
In other words, if you are running an office with no access control, you are running an office with gaping security holes.
Access Control Devices and Their Relevance For Our Daily Life
Access control isn’t just for businesses, now homes and residential buildings are using smart access systems to bring safety and convenience to occupants.
In everyday life these devices provide:
• Safer Access for Families
• Remote Lock / Unlock from with your Favorite Apps
• One- Time or Temporary Codes for Guests or Staff Servi
• Notifications and Alerts When Someone Comes In
• Theft protection and unauthorized access
They simplify your life and secure your home, or business, one device at a time.
Access Control Equipment Is Essential, Not Optional
In an era of increased security threats, digital workplaces, and remote administration, the access control devices have come to be a staple of modern security. They guard people, buildings, and information— making sure that only the appropriate people access at the right time.
Whether you are managing an office, running a business, or just want a secure home, purchasing access control devices is important for the safety of your peace of mind and your place in the future.
Importance for visitor management and employee attendance monitoring
The access control systems of today simplify the work at the office:
• Wages calculations are simplified because of automated attendance monitoring.
• HR and payroll benefit from accurate hours worked.
• Every individual entering the building is logged on the visitor logs.
• Live monitoring enables safer workplaces for management.
• Reporting for compliance is accelerated and more dependable.
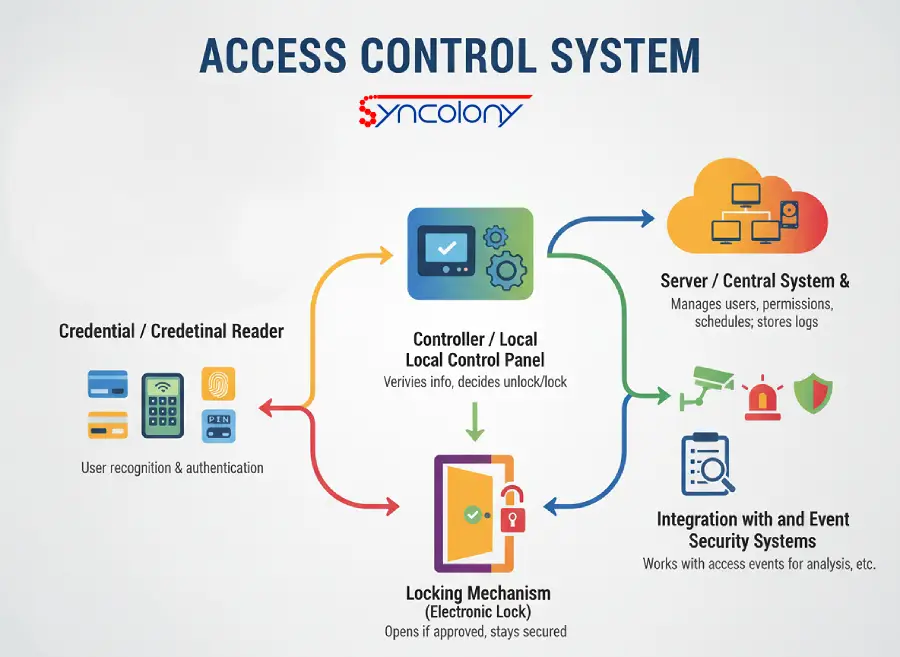
Parts and Configuration of a Access Control Unit / System
An access control system consists of multiple critical elements, each of which has a role to play in the security it provides.
Part | Role / Function
1. Credential / Credential Reader
The user is identified and authenticated by the use of RFID cards, PINs, magnetic cards, or biometric authentication.
2. Controller / Local Control Panel
The controller confirms the data as soon as a credential is offered and then either open the door or keep it locked.
3. Locking Mechanism (Electronic Lock / Door Lock)
When the credential is authorized, the electronic lock is released otherwise the door remains locked.
4. Server / Central System & DB
Testament to a better security administration, the server also handles users, roles, access schedules and retains logs of activity.
5. Logging, Audit, and Event Monitoring
All access events—entries, exits and failed attempts—are logged for use in security analysis and investigating incidents.
6. Integration with Other Security Systems
Seamlessly integrates with CCTV cameras, alarms, and other security solutions to provide extra security and centralized management.
Summary of Key Concepts Related to Access Control Devices (From ScienceDirect Insights)
Access control devices are security elements with the purpose of controlling who can enter, what can be accessed, and how resources are protected in physical and virtual environments. Their function is to prevent any unauthorized access to a physical location, system or data. ScienceDirect offers comprehensive access control device.
What Do Access Control Devices Do?
Access control mechanisms enforce security policies by:
• Authenticating identities with passwords, PINs, keycards, handheld biometrics, or mobile credentials
• Granting or denying access to rights holders in accordance with the policy rules
• Log access events for auditing and surveillance
•Extending to alarms, cameras and IT systems for enhanced protection
These devices act as the first level of defense in keeping unauthorized users out, whether they’re after your physical space, network, or computer. See more on access control Technology ScienceDirect.
Access Control As A Cybersecurity Challenge
In digital systems, access control can be used to:
• Authenticate users and software applications;
• Limit access to files, computer networks, or databases; and/or
• Block cyberattacks, such as a data exfiltration, unauthorized privilege escalation, or an insider attack. Contemporary access control schemes like RBAC, ABAC, and MAC, enable organizations to administer permissions and dynamically enforce security policies in a scalable manner. These protocols are fully outlined and analyzed in the ScienceDirect access control study.
Control the access Physical security devices in the room
The physical access control devices are crucial for regulating access to a building, room, or protected location. The following are the important accessories:
• Card readers and keypads
• Biometric scanners (fingerprint, facial recognition, iris)
• Electronic door and IoT locks enabled
• Turnstiles and security gates
• Controllers and panels that define access rules
These units are in constant communication with the networked access control system and are able to make instantaneous determinations as to who has access to a given location. For more technical information, go to ScienceDirect’s explanation of access control devices.
The Importance of Access Control Devices
Through access control devices Security risks can be greatly mitigated, ScienceDirect reports, including:
• Unauthorised entry
• Theft and vandalism
• Attacks on cyber-physical systems
• Threats from the inside
“Enabling progressive security through advanced access control is no longer a choice, but now a basic prerequisite for office, factory, hospital, data center, and government location in a high-threat world.”
Automation and Integration
Typical access control systems trends are:
• IoT connectivity to monitor access in real time
• Cloud-based management to manage remotely
• AI-based threat detection and behavior analytics
• Integration with cameras, alarms, and other security devices
With these new features, access control systems can help organizations automate security, mitigate human error, and grow effectively as they scale.
Relevance in Everyday Life
Access control systems are not just for businesses, now you’ll find them used in: Apartment complexes and houses are going smart with:
• Safer access for your family
• Lock/unlock from anywhere with mobile apps
• Temporary or single use codes for visitors and workers
• Real-time alerts and notifications upon entry
• Better protection from theft and break-in
With the right smart access control solutions, households and businesses alike can benefit from increased safety, convenience, and efficiency.
Ready to Upgrade Your Security with the Right Access Control System?
Our specialized team is ready to assist you in purchasing the best access control device or assist you in selecting the best biometric face recognition systems, time attendance terminals, and/or door access control panels. We assist our customers to select suitable products that fit their level of business security needs, budget, and growth multipliers over the years.
If you are in the market for face recognition access control, RFID card reader, smart gate entrance systems, or as complex as an access management solution for your facility, we eliminate the guesswork in selecting the products that best fit your business needs.
Reach out to our team of security experts for a complimentary needs assessment and device comparison, and the best access control systems customized for your office, warehouse, retail, or residential property. We aim to give you the security you deserve and build it to be more robust, intelligent, and ready for the future.


